Internet 101 - Encryption and security
Symmetric and asymmetric encryption concepts, the most known cybercrimes ...
We share a lot of data on the Internet. Our credit card, bank information, passwords we use when entering any system are also included in this data sharing. So how is this information kept safe? If we sent the data as it was, somebody would pull our package, open it, read it, then release it. We won't even know what was happening because the package would reach the destination. Mixing and modifying data are made against such dangers. This process is encryption. It must also be decrypted when it reaches the goal.
One of the oldest known encryption methods in history is "Caesar cipher". In this method, the transceiver determines a mutual key number and then scrolls the alphabet by this number for each letter. For example, if "3" is the selected keyword, go forward 3 and write D instead of the letter A.
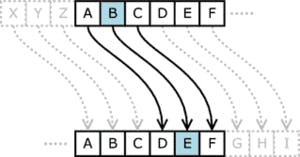
The danger of encrypting with the Caesar cipher method is that it can be found after attempts in the alphabet. If a key was not just a number but for example 10 key numbers, like 1 number for the 1st letter, another number for the 2nd letter. That would make things even more difficult, of course, at least for a human being, but it would still take a few seconds for a computer. So what should we do to make things difficult for our password not to be easily decrypted?
Today's secure communication channels are encrypted with 256-bit keys. This extends the brute force attack period considerably. This encryption method, which seems to be sufficient for today, will change with new ones as time passes. The receiver and the transmitter have the same key, and this way of encryption and decryption is called "symmetric encryption". This shared key must be decided upfront in a secret way. The idea might have been if people had come face to face, but it's hard to do on the internet. That's why the internet uses "asymmetric encryption". In asymmetric encryption, there is a public key that is shared with everyone and a private key that is not shared.
Anyone can encrypt data with the public key, but only the data with the private key can be viewed.
Let's say we have a mailbox, two parts with keys, one to store mail and one to receive. You don't want anyone to access your mail, so you don't give the key to the mail receiving part to anyone, but you don't want to prevent mail from coming, so you can hang it nearby at the mailbox and you can make the key available to everyone. In this way, communication was provided securely without the need for private keys on both sides. Security is provided with encryption using this method in TLS and SSL protocols.
The most known cybercrime are virus, DDoS attack, Phishing. The virus comes into our computer involuntarily, through another program, or our carelessness. What happens after you arrive? It can delete our files, stole them, control our programs, control our computer remotely. All of this sounds horrible, right? Using these viruses, your computer may be captured and become a "botnet", so you may unknowingly join the army in another major attack. This army may not be as glorious as you think, maybe you may even collapse your country's system and make your own life difficult. Such attacks are known as DDoS (Distributed Denial Of Service). This attack aims to crash a system by overwhelming it with demand. During the excessive demand, they use the army they established before. Another method may be to use our data and steal our money by logging into the system by accessing our password and username information by deceiving via e-mails. This method is known as phishing.
In this article, I wanted to make a brief introduction to security concerns on the internet. To access the Internet 101 series:
- What is the internet, how does it work? Who is the owner?
- Internet 101 - IP and DNS
- Internet 101 - How data is transmitted?
Resources:
